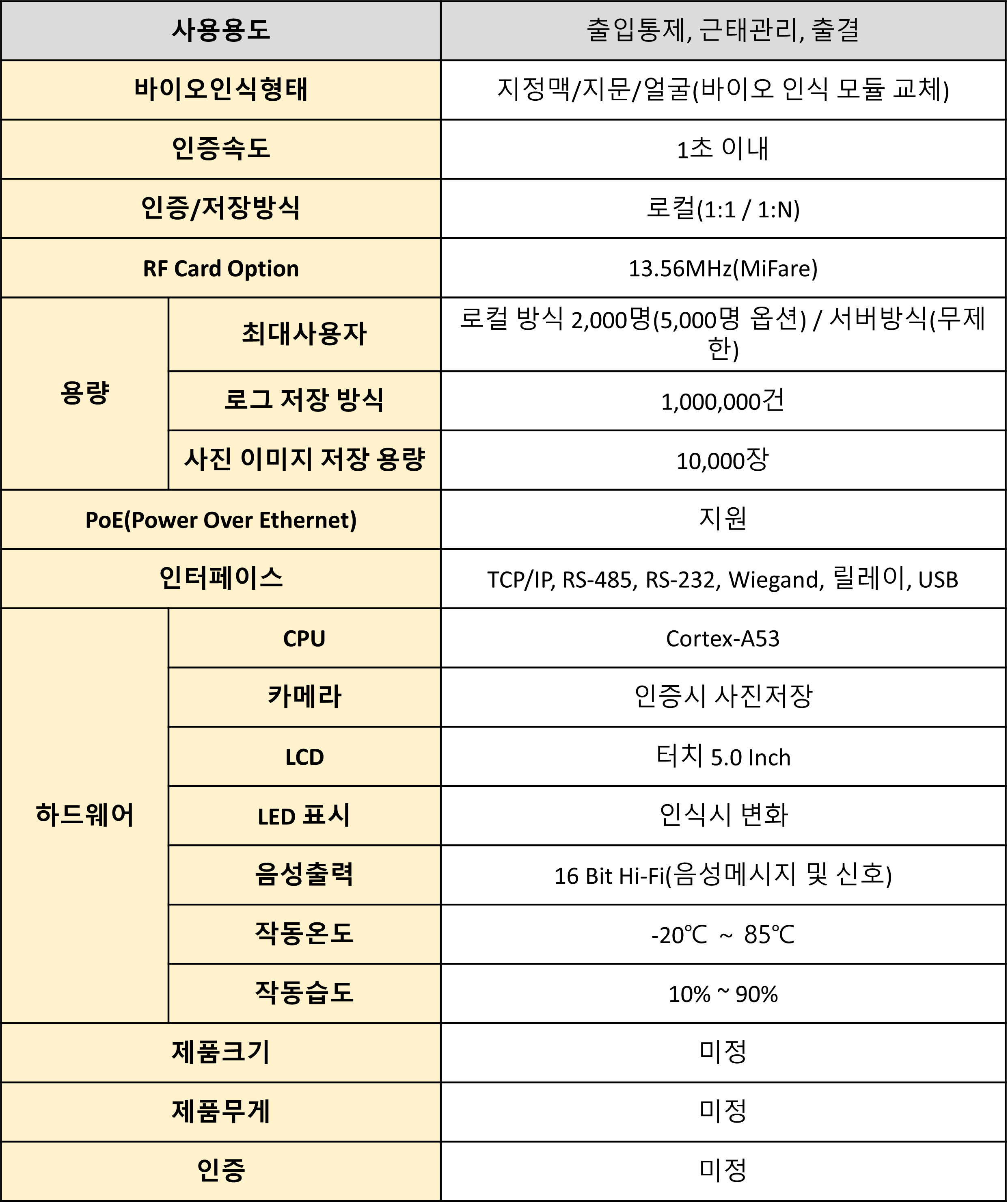
In today’s society, we are immersed in the digital world. Our information and valuable data are constantly transmitted and stored through the internet.
And all access and security begin with a small string of characters called a password.
Passwords serve ase the guardians of our digital realm, but often this small guardian is not suitable of protecting us.
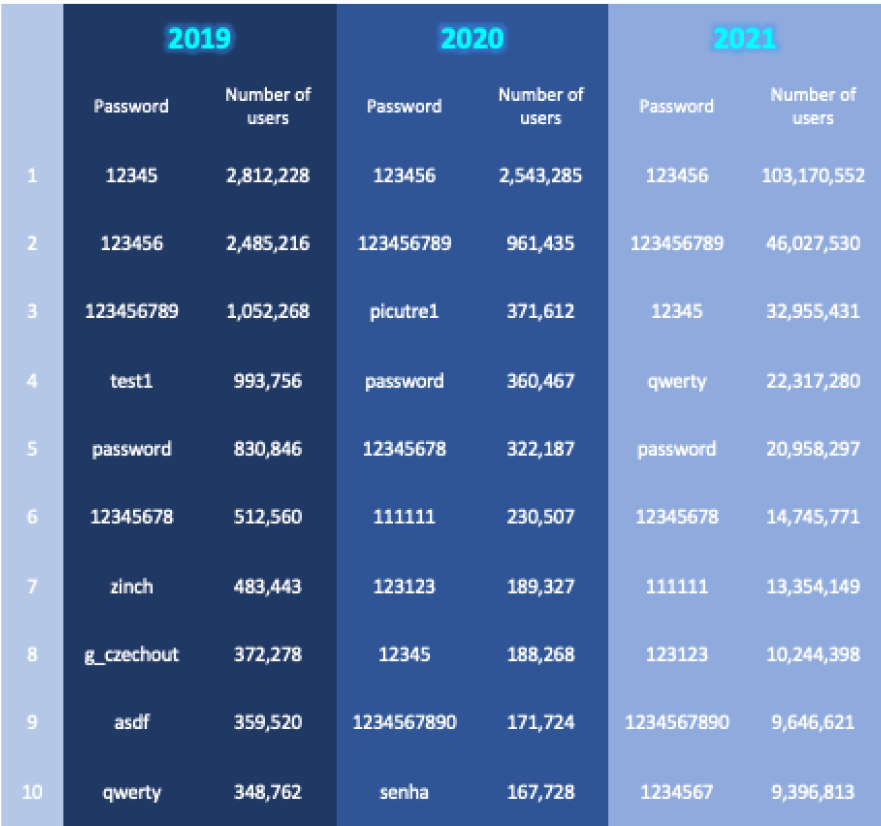
Top 10 most common passwords of the year 2019-2021
In reality, many people around the world are currently using simple number combinations like ‘123456’ as their passwords.
Such simple passwods can be hacked within seconds and cause significant harm to users.
Despite the continuous warnings from cybersecurity experts about the consequence of irresponsible password management, we can still observe the vulnerability in security through the most commonly used passwords between 2019 and 2021.
Password Reuse
Since many users reuse the same password across multiple accounts, if one account is compromised, all other accounts using the same password are also at risk of exposure.
Password Theft
Password Theft
Password Complexity
Strong passwords that are difficult to guess are often complex and hard to remember, leading users to write them down or store them in insecure locations.
Lack of Scalability
As the number of online accounts and services requiring authentication continues to increase, the use and management of usernames and passwords are becoming increasingly cumbersome and challenging.
Inherent Security Vulnerabilities
Usernames and passwords are inherently insecure due to the possibility of password guessing or theft. Even if a password is long and complex, it can still be vulnerable to brute-force attacks or other types of password-cracking techniques.
It is challenging to maintain a balance between security and usability.
Easy-to-remember passwords are not secure, while secure passwords are difficult to remember.
Due to these issues associated with password usage, there is a need for alternative authentication methods that are both safer and more convenient.
What are the alternatives?
Biometric Authentication
Biometric authentication methods, based on unique physical characteristics, can provide a more secure and convenient way of authenticating users.
Biometric authentication offers several advantages over traditional methods such as passwords or PINs.
Enhancing Security
Biometric authentication is difficult to forge or steal since it is unique to each individual. Therefore, it provides robust defense against identity theft and other forms of fraud, making it a highly secure authentication method.
Convenience
Biometric authentication is fast, convenient, and eliminates the need to memorize passwords or other codes. Therefore, it is an ideal solution for situation where speed and convenience are crucial, such as online banking or mobile payments.
Improving User Experience
Biometric authentication, which eliminate the need for passwords or other codes, can greatly enhance the user experience. This can lead to higher levels of customer satisfaction and greater user adoption.
However, it is important to be aware of the strength and weakness of each biometric authentication method.
• FingerPrint Recognition
FingerPrint Recognition
Strength
1. The most widely adopted biometric authentication method worldwide.
2. It offers good accessibility and fast recognition speed during biometric data enrollment.
3. It eliminates the need for separate issuance of employee ID cards or access cards, resulting in relatively low maintenance costs excluding initial investment.
Weakness
1. Vulnerable to spoofing using high-quality fingerprints or 3D printed replicas.
2. Difficult to accurately identify users with worn-out fingerprints, particularly among certain occupations.
3. Susceptible to environmental factors such as dust or moisture, which can negatively impact accuracy.
• Facial Recognition
Strength
1. Less resistance compared to other biometric methods as it uses cameras for recognition.
2. Individual faces have unique features and patterns, resulting in high recognition rates.
3.Offers high speed and accuracy in recognition, and allows for convenient walking-through scenarios.
Weakness
1. Prone to errors when identifying individuals with darker skin tones or unique facial features.
2.Vulnerable to spoofing as facial photos or videos can be used to device the system.
3. Changes in appearance such as cosmetic procedures, plastic surgery, presence of glasses or facial hair can impact accuracy.
• Iris Recognition
Strength
1. Offers superior security compared to fingerprint or facial recognition.
2. The iris is formed by around 18 months of age and remains unchanged throughout a person’s lifetime, making it suitable as an authentication method.
3. Allows for contactless recognition.
Weakness
1. Some users may find it uncomfortable or challenging to maintain direct eye contact with the camera for a few seconds.
2. Changes in lighting conditions or reflections can affect the accuracy of iris recognition technology.
3. Certain medical conditions or eye injuries can make it difficult or impossible to capture accurate iris images.
• Finger Vein Recognition
Strength
1. Vein patterns are located inside the finger, making them unaffected by external environmental factors.
2. Utilizing the veins located inside the finger makes forgery, hacking, and tampering difficult.
3. Offers high speed and accuracy in recognition, with lower setup costs compared to iris recognition.
Weakness
1. Due to the requirement of specialized equipment, it may be challenging to apply it easily in all locations.
2. Even with the same finger, the recognition results can vary depending on the placement, which can affect accuracy.
3. There are limitations in the collection methods of vein data.
• FingerPrint Recognition

Strength
1. The most widely adopted biometric authentication method worldwide.
2. It offers good accessibility and fast recognition speed during biometric data enrollment.
3. It eliminates the need for separate issuance of employee ID cards or access cards, resulting in relatively low maintenance costs excluding initial investment.
Weakness
1. Vulnerable to spoofing using high-quality fingerprints or 3D printed replicas.
2. Difficult to accurately identify users with worn-out fingerprints, particularly among certain occupations.
3. Susceptible to environmental factors such as dust or moisture, which can negatively impact accuracy.
• Facial Recognition

Strength
1. Less resistance compared to other biometric methods as it uses cameras for recognition.
2. Individual faces have unique features and patterns, resulting in high recognition rates.
3.Offers high speed and accuracy in recognition, and allows for convenient walking-through scenarios.
Weakness
2.Vulnerable to spoofing as facial photos or videos can be used to device the system.
3. Changes in appearance such as cosmetic procedures, plastic surgery, presence of glasses or facial hair can impact accuracy.
• Iris Recognition

Strength
1. Offers superior security compared to fingerprint or facial recognition.
2. The iris is formed by around 18 months of age and remains unchanged throughout a person’s lifetime, making it suitable as an authentication method.
3. Allows for contactless recognition.
Weakness
1. Some users may find it uncomfortable or challenging to maintain direct eye contact with the camera for a few seconds.
2. Changes in lighting conditions or reflections can affect the accuracy of iris recognition technology.
3. Certain medical conditions or eye injuries can make it difficult or impossible to capture accurate iris images.
• Finger Vein Recognition

Strength
1. Vein patterns are located inside the finger, making them unaffected by external environmental factors.
2. Utilizing the veins located inside the finger makes forgery, hacking, and tampering difficult.
3. Offers high speed and accuracy in recognition, with lower setup costs compared to iris recognition.
Weakness
1. Due to the requirement of specialized equipment, it may be challenging to apply it easily in all locations.
2. Even with the same finger, the recognition results can vary depending on the placement, which can affect accuracy.
3. There are limitations in the collection methods of vein data.
If we understand the advantage and disadvantages of biometric identification technology and use it appropriately in accordance with the situation and environment, it can become an effective tool for identity verification. Therefore, choosing the appropriate biometric authentication technology based on the environment and level of security is crucial.
eTunnel Inc. will protect your safety through services tailored to your situation and environment in physical security and cyber security.